Understanding the Cyber Kill Chain: A Blueprint for Cyber Defense
In the realm of cybersecurity, staying ahead of attackers begins with understanding how they operate. The Cyber Kill Chain, developed by Lockheed Martin, is a proven model that breaks down the steps cybercriminals take to breach systems. By dividing the attack process into distinct phases, cybersecurity professionals can detect, disrupt, and mitigate threats before significant damage occurs.
This blog post delves into each step of the Cyber Kill Chain, highlighting its importance in defending against modern cyber threats.
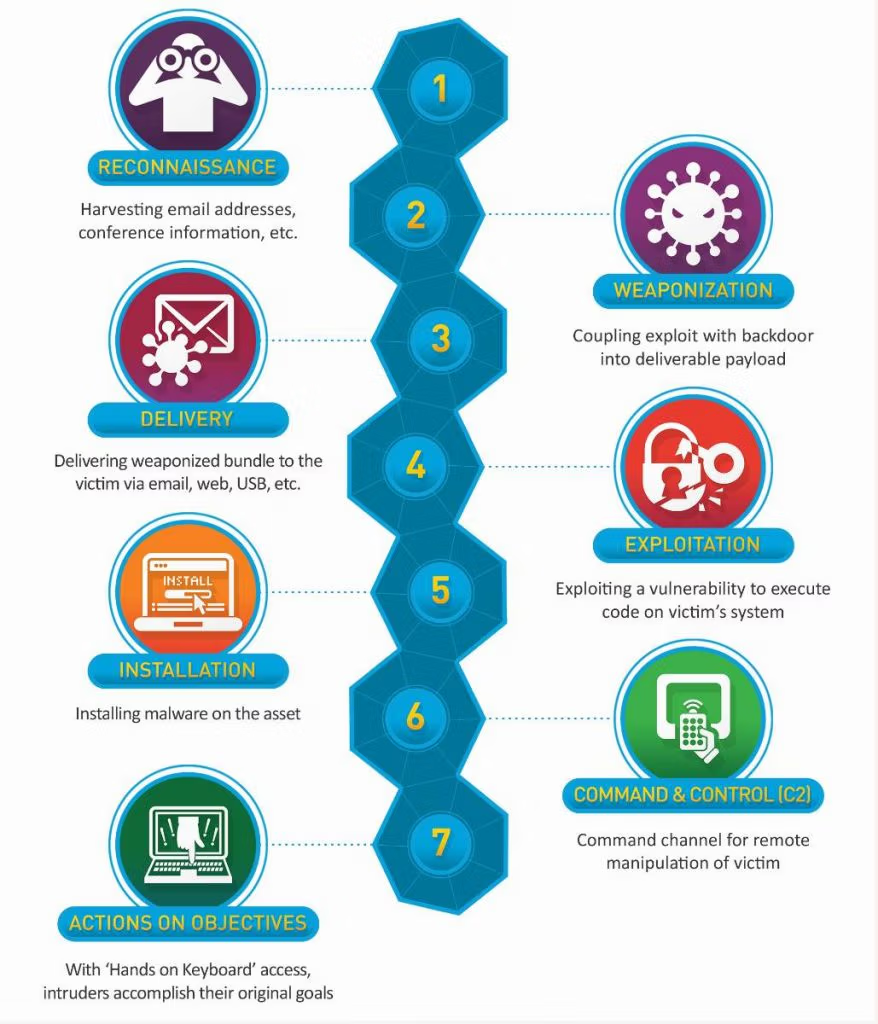
Step 1: Reconnaissance
The first phase involves attackers gathering information about their target. They research organizations, employees, systems, and potential vulnerabilities using methods such as scanning websites, analyzing publicly available data, and phishing attempts.
Why It Matters:
Identifying reconnaissance activities, like unusual network scans, can help predict and prevent attacks.
Security awareness training reduces the risk of successful phishing attempts.
Step 2: Weaponization
In this stage, attackers develop tools or payloads, such as malware, viruses, or malicious scripts, to exploit identified vulnerabilities.
Why It Matters:
Threat intelligence analysis helps predict attackers’ tools and tactics.
Keeping systems and software updated eliminates exploitable vulnerabilities.
Step 3: Delivery
The attacker delivers the malicious payload to the target using phishing emails, malicious links, infected USB drives, or compromised websites.
Why It Matters:
Email filtering, web security, and sandboxing tools can intercept malicious payloads.
Educating users about phishing drastically reduces delivery success rates.
Step 4: Exploitation
Once the payload reaches the target, attackers exploit system vulnerabilities to execute their attack, such as running malicious code or escalating privileges.
Why It Matters:
Regular vulnerability scanning and timely patch management reduce exploitable weaknesses.
Intrusion detection systems (IDS) can spot unusual activities signaling exploitation.
Step 5: Installation
Here, attackers install malicious software (e.g., malware, ransomware, or spyware) to maintain a foothold in the system and prepare for further actions.
Why It Matters:
Endpoint monitoring can detect suspicious installations or system changes.
Endpoint detection and response (EDR) tools add an extra layer of security.
Step 6: Command and Control (C2)
Attackers establish a communication channel between their malicious software and their systems, enabling them to control compromised devices remotely.
Why It Matters:
Network monitoring can identify and block unusual outbound traffic.
DNS filtering and traffic analysis can disrupt attacker communications.
Step 7: Actions on Objectives
In the final stage, attackers execute their objectives, such as stealing data, encrypting files for ransom, or disrupting operations.
Why It Matters:
Proactive monitoring for data exfiltration and unauthorized access minimizes damage.
A well-prepared incident response plan ensures rapid recovery and damage mitigation.
Strengthening Cyber Defense with the Cyber Kill Chain
The Cyber Kill Chain provides a powerful framework for understanding and addressing cyber threats. By dissecting an attack into manageable phases, organizations can implement proactive measures, including employee training, vulnerability management, and advanced monitoring tools, to thwart attackers at every step.
Leveraging this model allows cybersecurity teams to predict attacker behavior, reduce risks, and build a more resilient security posture in the face of evolving threats.

Sammy Cordero
Consultant
I’m a cybersecurity consultant with a degree in Information Technology and a Cybersecurity Certification from ISC2. As a member of the ISC2 New Jersey Chapter, I’m dedicated to educating communities on scam prevention and digital safety. At CyberAdversaries.com, I break down complex cyber threats into clear, actionable insights to help individuals and organizations stay secure in a rapidly changing digital world. Feel free to contact me for cybersecurity consulting services tailored to your personal or business needs.
Copyright © 2025 Cyber Adversaries Blog | Powered by Cyber Adversaries Blog
